There are many potentially valid reasons you may want to be discriminate to countries on your personal computer or your network infrastructure.
- Distinct country-specific locality of your users or the resources you use.
- Distinct intensity of cyber attacks or threats.
- Legal restrictions (data protection laws, trade sanctions).
Particularly relevant, novel motivation as of March 2022 is the boycott of Russia in response to the invasion of Ukraine.
This is a purely technical article about how this can be achieved and what to expect as a result. It’s your responsibility to assess the upsides, downsides and potential damages of such change in your case.
Nothing technically special about Russia in this regard - these instructions should apply to blocking any other country, Russia serving simply as a representative example.
OpenWRT is a well-known and long-established Linux distribution targeting popular low-power routers. It allows individuals to obtain ultimate control over their home or office network within reasonable efforts. It features a beginner-friendly web interface, LuCI. OpenWRT matters because typical consumer-grade network routers have very limited management functionality and there’s no way to achieve our goal.
If you want to block Russia on your servers which run other Linux distributions, please wait for my following articles, where I intend to cover it for the most popular setups such as Ubuntu, Debian and others.
So how we do it?
We will address the problem at multiple layers.
Block Russian top-level domains (TLD) in DNS Link to heading
Your local router acts as an intermediate DNS server, handling domain name resolution requests.
It is trivial to tell it to effectively reply “no such domain” to any domain in .ru, .su and .рф TLDs.
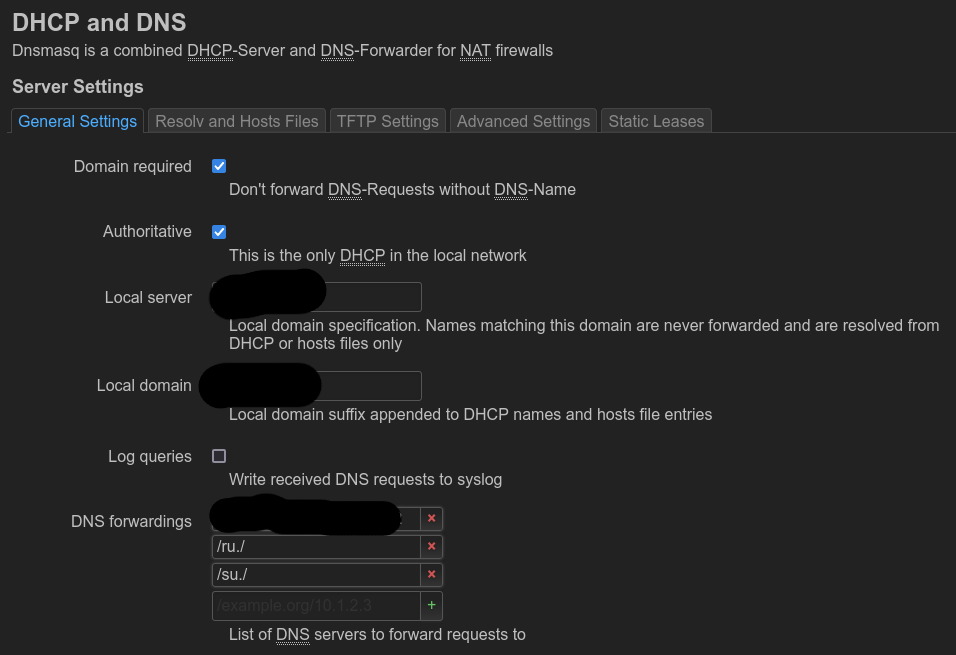
Navigate LuCI web interface: “Network” -> “DHCP and DNS”.
Add entries into “DNS forwardings”, looking like this: /ru./, /su./.
This means: for the domain names rooted in these TLDs, don’t do any lookups.
Entering /рф./ appears to not work here currently.
Test Link to heading
Try accessing any domain in the blocked zones. This should fail now.
For example, you can use one of the widely available DNS diagnostic tool in a Linux terminal. The result should look like this:
$ nslookup lenta.ru
Server: XX.XX.XX.XX
Address: XX.XX.XX.XX#53
** server can't find lenta.ru: NXDOMAIN
Block Russian IP addresses Link to heading
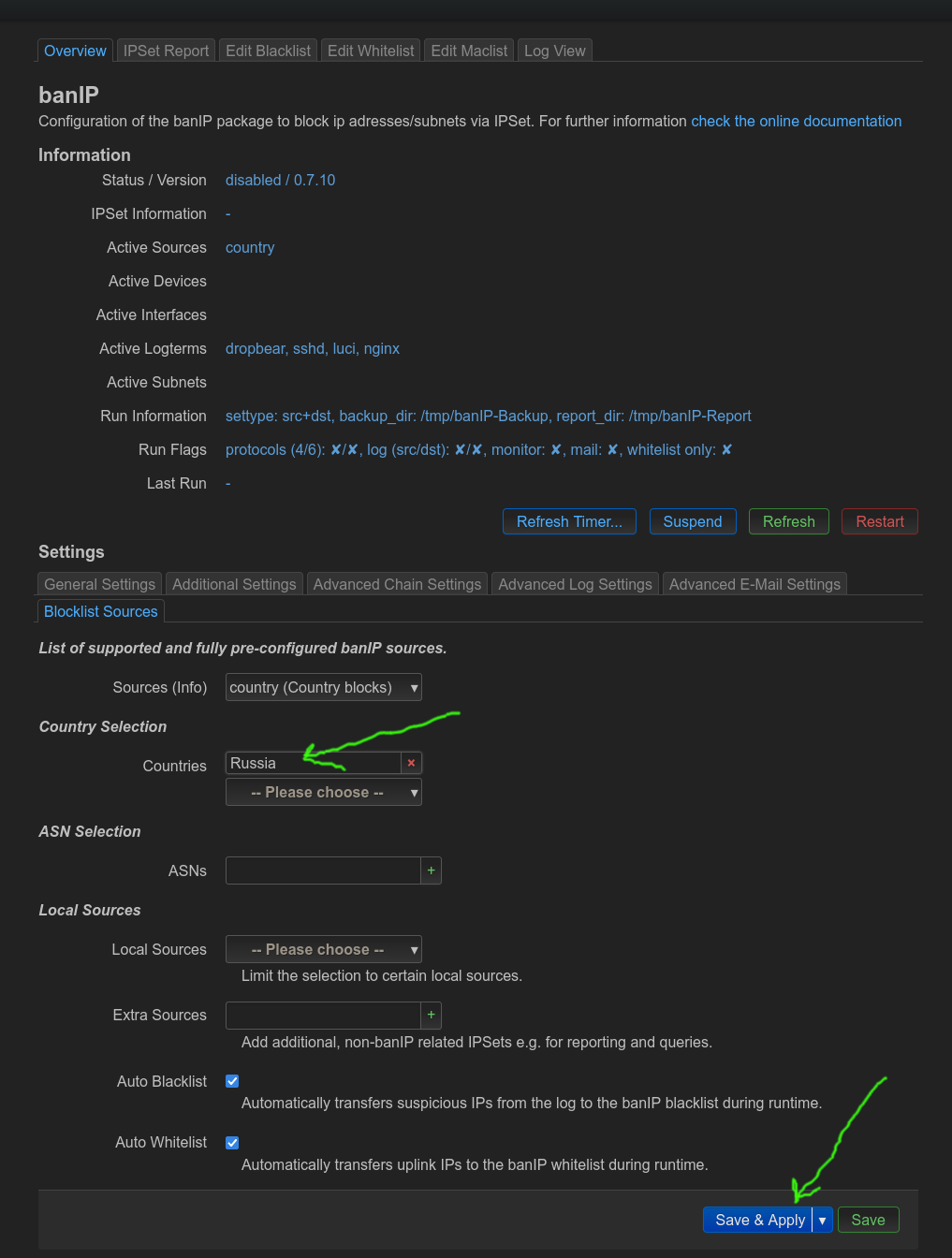
OpenWRT conveniently provides a banIP service and a web interface for it.
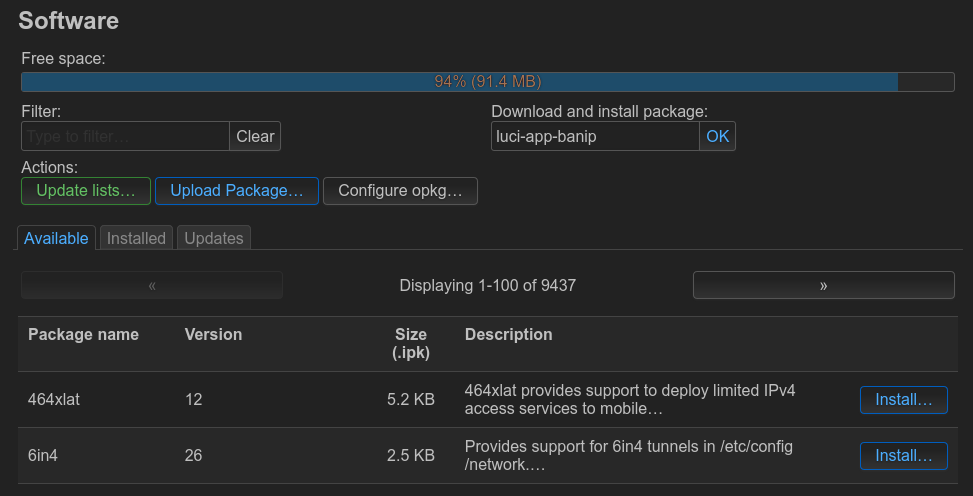
To install it, in LuCI go to “System” -> “Software” and opt to install luci-app-banip and banip packages.
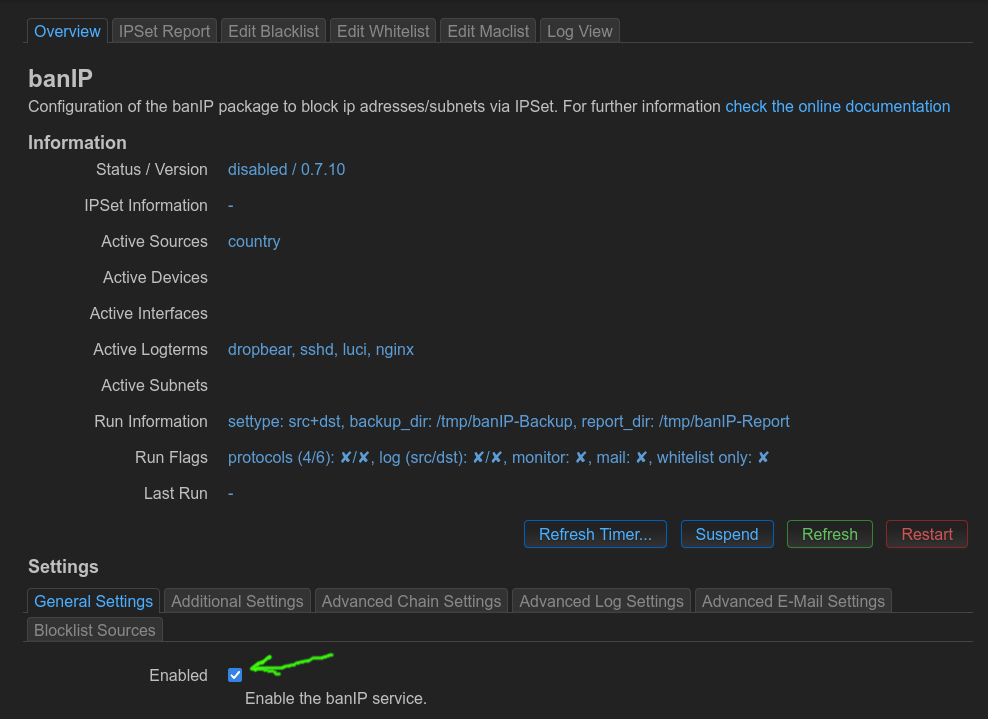
Then go to “Services” -> “banIP” in the top menu.
Tick the “Enable” checkbox to enable the service.
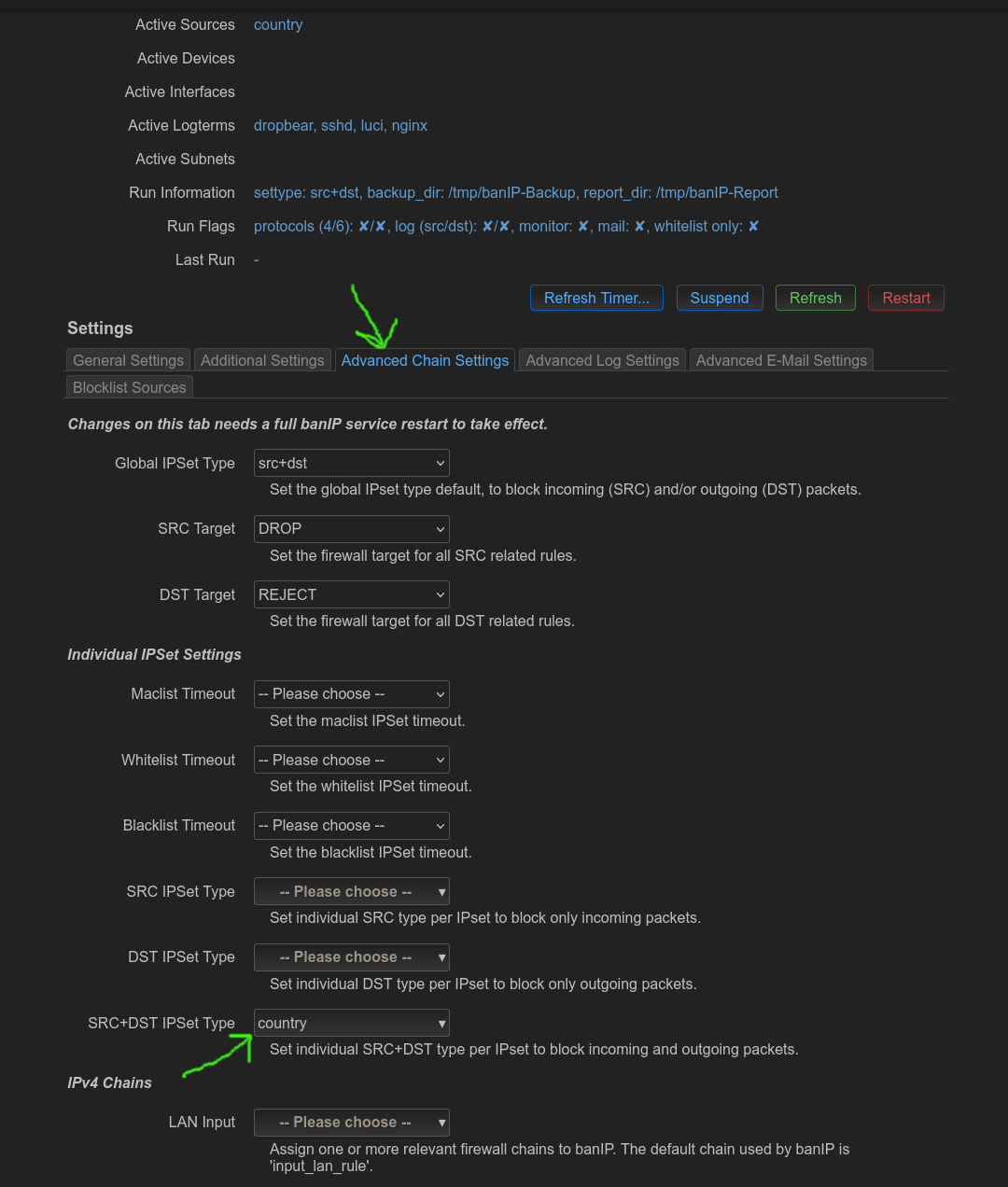
Switch to “Advanced Chain Settings” tab. Set “SRC+DST IPSet Type” to “contry”.
Switch to “Blocklist Sources” tab.
In “Countries”, select “Russia”.
Press the button “Save & Apply”.
Test Link to heading
It’s easier to test this while having the earlier DNS blocking disabled. Then you’d send requests or pings to some russian domains and expect get connection timeouts.
Ideally you would expect that to work every time, but what I found my testing is that it’s not so: websites such as lenta.ru and yandex.ru were not blocked. On the other hand, livejournal.com was blocked as a result.
So keep in mind that geographical IP address attribution is never 100% accurate. Still, ipdeny.com which is the source of the data for this blocking has existed for a long time and is well regarded. You can add your own whitelists and blacklists right here in banIP settings. You may also be interested in other IP lists banIP brings to your fingertips: there are many independently cyberthreat blocklist sources such as blocklist.de, FireHOL, Spamhaus, Emerging Threats, Cisco Talos and others.
Block known-Russian domains in other TLDs Link to heading
There are some web domains known to be affiliated with Russia which are not on russian TLDs, for example Russia Today is on rt.com.
You can supply OpenWRT with your text file with a compilation of domain names for which you want to override the default handling.
Form your blocklist text file in such form: <bad IP> <hostname string> # comment, one entry per line.
For example:
0.0.0.0 rt.com # Russia Today
0.0.0.0 www.rt.com # Russia Today
0.0.0.0 sputniknews.com
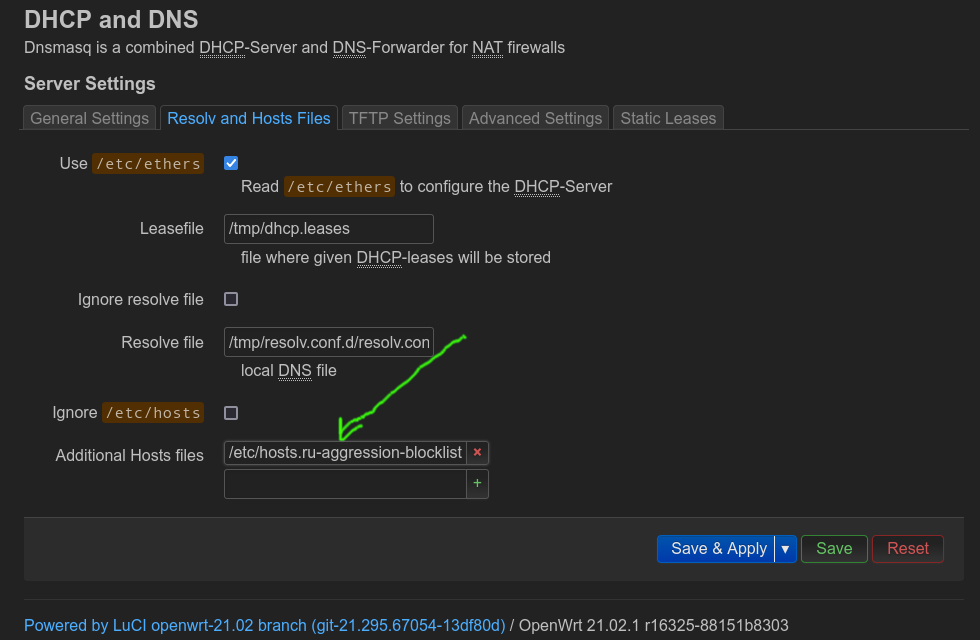
Copy your blocklist text file to the OpenWRT machine.
In LuCI web interface, go to “Network” -> “DHCP and DNS”.
In “Additional Hosts files”, specify a path where you put your text file on the OpenWRT machine. Press “Save & Apply”.
Please contact me to suggest additional entries!
Test Link to heading
After making this change, connections and pings to the listed domains should not work.
Conclusions Link to heading
That’s the extent to which OpenWRT can easily help us to block all connections with Russian-controlled part of the Internet. Of course, there are always creative ways to do more to achieve a more consistent, resilient and future-proof result.
But most importantly, remember that the ultimate firewall is your head.
See another article: How to block Russia on your servers.